Advice for companies affected by the upcoming NIS Directive
On the 28th January, 2018, the UK’s National Cyber Security Centre published guidance on the upcoming Network Information Systems (NIS) Directive, which is set to come into force on the 9th May this year.
The Directive is one of the most important pieces of cyber security legislation to hit the UK yet. But in recent months, it’s largely been overshadowed by GDPR. Unlike GDPR, the NIS Directive has rarely made headlines and is far less likely to have been discussed in corporate board meetings.
Over the last few days, in certain sectors, that’s changed. The announcement of up to £17m fines has become the focus of many a recent news story, and affected parties have begun looking into what they can do to avoid the fines.
Unfortunately, avoiding fines is the wrong objective. As with GDPR, the best way to avoid the fines is to stop trying to avoid the fines in the first place.
The NIS Directive is not a money making scheme
The NIS Directive isn’t a money-making scheme. The UK government isn’t introducing the legislation to raise funds. What they’re hoping to achieve is better security for essential services – hence the Directive applying to critical industries only.
NIS Directive: Who is Likely to be Affected?
-
-
-
- Water and Electricity Suppliers and Providers
- Oil Producers, Processors and Distributors
- Gas Transmitters, Distributors, Refinement and Storage Providers
- Healthcare Providers
- Air, Rail, Maritime and Road Transport Providers
- Digital Infrastructure Providers (incl. Top Level Domain Name Registries, Domain Name Service Providers and Internet Exchange Point Operators)
- Digital Service Providers (DSPs) (incl. Cloud Computing Providers (SaaS, PaaS, IaaS), Search Engine Providers and Online Marketplace Providers)
-
-
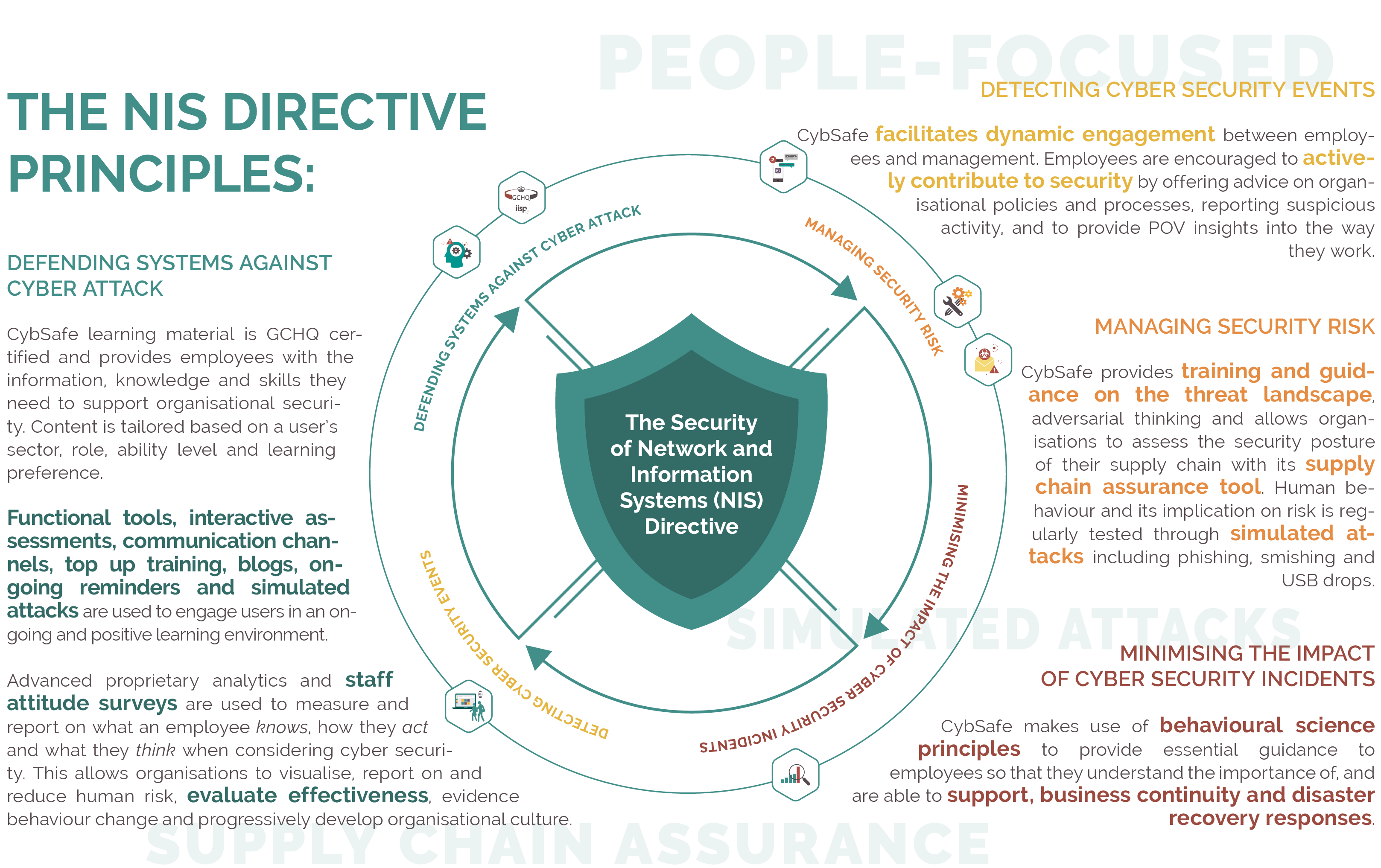
To truly comply with the Directive, organisations should shift their focus from avoiding fines to: managing security risk; improving defences; and detecting and combating security incidents – because doing so will both avoid fines and improve defences at the same time.
Doing all that, of course, isn’t easy. It requires technological solutions and robust security processes. But, most of all, it requires engaged and secure people.
The people problem
Unfortunately, engaged people who know of the importance of information security and behave in a secure manner are hard to come by.
Security training has been around for decades now. In many industries, it’s mandatory. But, to take a recent example, fewer than 10% of today’s Gmail users have bothered to enable two-factor authentication.
Today, even when people know about the risks, awareness isn’t triggering secure behaviours. Tick-box training isn’t working – and the NIS Directive calls for training “based on an understanding of how people really work with the systems” and the development of “a positive security culture” suggest the UK government favour a different approach.
An intelligent alternative
Fortunately, tick-box security training is no longer the only training option available.
The CybSafe platform was (and continues to be) developed alongside behavioural psychologists to do more than improve what people know about security. Content is GCHQ-certified and tailored to an individual’s sector, role, ability level and learning preference. As well as imparting knowledge, the platform shifts people’s perceptions of security and demonstrably changes behaviour in practice.
When combined with legislation such as the NIS Directive, platforms like CybSafe have the potential to usher in an era in which people are no longer seen as a security hazard but instead as a security asset. So long as organisations are willing to change their approach…
Overcoming biases
How likely are organisations to change their approach to security training?
When drafting the NIS Directive, the UK government asked a sample of stakeholders if they planned to make additional security related investments as a result of the Directive.
42% said they would – which seems high. But it also suggests 58% of people plan to continue with existing strategies, despite the new Directive.
It could be that 58% of people are ahead of the game. But, given almost half of all UK businesses identified at least one cyber security breach or attack in the 12 months before April 2017, that seems unlikely.
What’s more likely is at least some of the 58% are suffering from status quo bias; an innate psychological quirk that causes people to prefer the current status quo to alternatives, even when alternatives are rationally beneficial.
Such biases demonstrate one of the major challenges the security industry is currently facing: people are not entirely rational. If we were, improving security would be as simple as explaining the risks.
The new era
All that said, the NIS Directive is undoubtedly a positive step.
The changing law shows the UK government no longer believes the status quo is acceptable.
Alongside GDPR, the Directive could help usher in a new era of security – a time in which people are no longer seen as a weakness but as the defence they should be.
We just need to stop focusing on the fines – and instead start focusing on improving security as a whole.