Integrating stories into security awareness training increases the chances of people remembering information, and relaying it to loved ones.
We use story-style training at CybSafe. Below you’ll find one of our modules that tells the story of notorious prankster James Linton. This is how he duped the White House…
The true story of a prank so good, even the White House fell for it 🃏
One slow day, whilst sitting in his office, James Linton noticed something. Emails don’t show the sender’s email address by default. He realised he could change the sender name to anything he wanted. So he did, for five months.
He started by pranking his colleagues. He sent them emails that looked like they were from their CEO. He loved the excitement and wanted more.
James’ first real victim was the CEO of a large British bank. James sent him an email purportedly from the bank’s chairman. Suspecting nothing, the CEO engaged in an exchange praising the chairman.
James leaked the email exchange, embarrassing the CEO and prompting the bank to reconfigure their email systems. SINON_REBORN – James’ prankster alter ego – had arrived!
The pranking spree continued.
The Governor of the Bank of England.
The CEO of not one, but two global investment companies.
And the White House!
Sending fake emails was exhilarating. James compared the excitement of it to the high of gambling – “You fire out three emails, and one of them comes up. When it does, you realise you have one on the line.”
James’ emails worked. Over and over again.
They worked because they won his victims’ trust.
That’s exactly what targeted fake emails do.
What are fake emails?
Fake emails look like they’re from legitimate or known sources, like a person or company you know.
These days, fake emails are difficult to spot.
The idea that most fake emails come from “long-lost relatives” is a myth. Today’s fake emails are more convincing. For the most part, they’re free from spelling and grammatical errors.
Fake emails can be either generic or targeted.
Generic fake emails are low in complexity but high in volume. Criminals send out millions of them. They usually look like they’re from a well-known company like Apple or Amazon.
Targeted fake emails are harder to recognise and are increasingly common. They’re unique to the recipient and usually reference information found on platforms like LinkedIn.
You may have heard some people refer to fake emails as “phishing”. They’re exactly the same thing. Targeted fake emails are sometimes called “spear-phishing”.
Creating legitimate-looking fake emails isn’t as hard as you might think.
How did James Linton create fake emails?
James decided on his target first. Then he picked his character based on his target’s professional and personal connections.
The next step was to find a hook. The hook was usually an interest both James’ target and character shared.
James then created a fake email address using his character’s name.
Finally, James added extra credibility to his fake emails. For example, he might hand type a second “email” below his message. This additional text, James believed, made his emails seem as though they had been forwarded.
James also favoured adding “Sent from my iPhone” to the end of messages. This made it seem like his messages were sent by an ordinary person, not “somebody huddled over a laptop in their hoodie.”
How to create legitimate-looking fake emails – A step-by-step guide by James Linton
1. Pick your target.
2. Pick your character.
3. Create a hook.
4. Create a fake email address.
5. Add extra credibility.
Ian Levy: a target too far
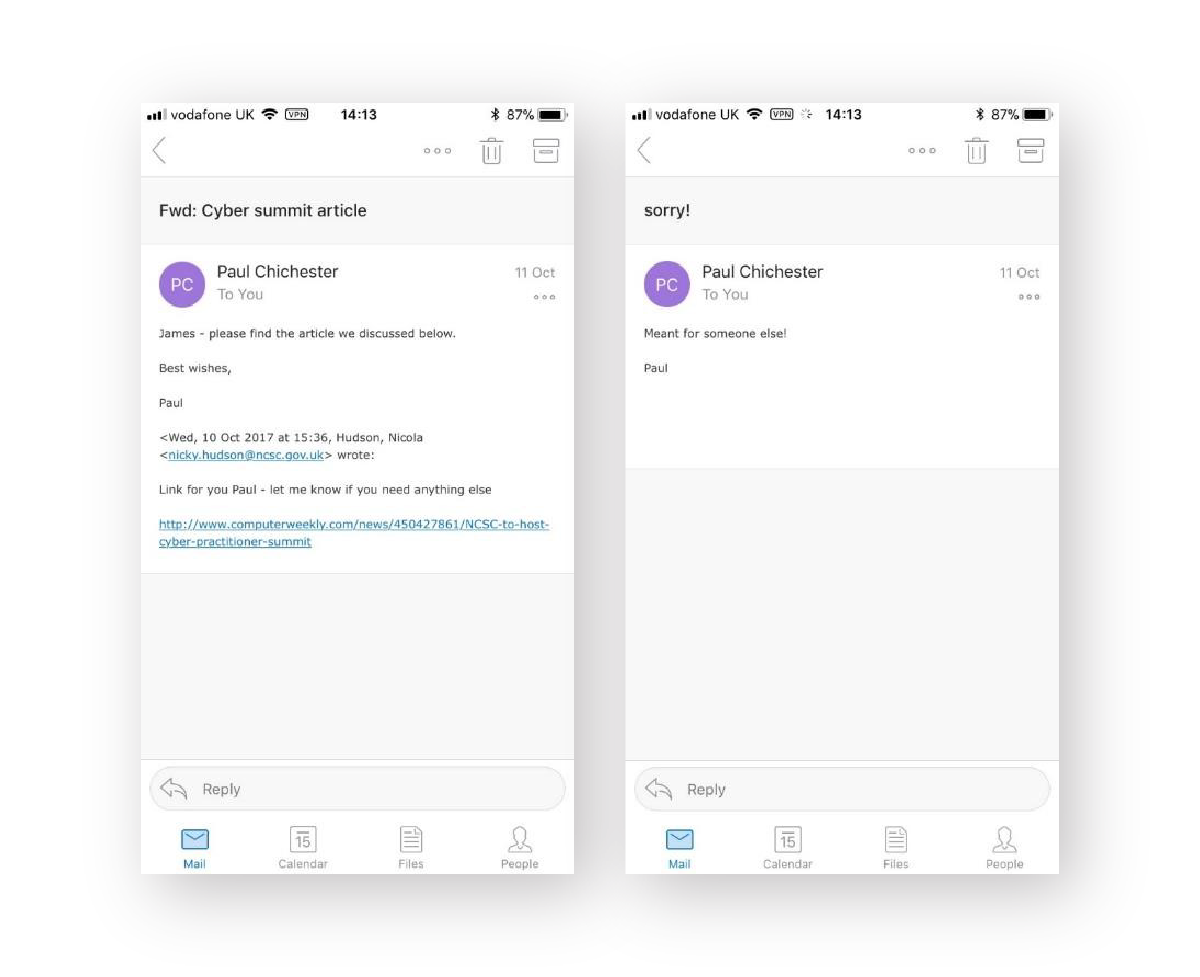
After tricking the White House, James’ search for worthy prey continued. That was when he landed on the Technical Director of the UK’s National Cyber Security Centre (NCSC) – Dr Ian Levy.
Posing as a colleague – the Director of Operations – James “accidentally forwarded” an email from another colleague – the Director of Communications – to Ian, including a link to an article.
After inspecting the link on this phone (by a good old “touch-and-hold”), Ian suspected the emails were fake.
How to spot fake emails
You can use Ian Levy’s 3-step checklist:
- Check the sender’s address.
- Check content.
- Check links or attachments.
✔️ Step 1: Check the sender’s address
Email inboxes show sender names, but they don’t always show addresses.
You can click on the sender’s name to reveal their actual email address. Pay attention to the information that comes after @.
Right after Ian had noticed the link protection of mail.com – instead of ncsc.gov.uk – he examined the sender’s address:
paul.chichester.ncsc.gov@mail.com
It didn’t look right. It was supposed to end with @gov.co.uk. He was intrigued, so he played along, humouring his adversary. Eventually, Ian Levy convinced James Linton to reveal his identity.
Do you recognise the sender or the sender’s email address?
- Click on the sender’s name to reveal their email address.
- Contact the person you think the email is from – using anything but that email address.
✔️ Step 2: Check content
Fake emails use emotional manipulation to trick people. Notice the different types of emotions evoked:
Panic 😱
Make a payment – your manager needs you to make an urgent payment.
Worry 😰
Verify some information – someone has tried to access a company or service you rely on (such as a bank, phone provider or TV service).
Curiosity 🧐
Open an attachment – you’ve been sent a confidential document to read. This is how James Linton attempted to trick Ian Levy. The emails “accidentally forwarded” from his colleague evoked curiosity.
Kindness ❤️
Visit a website – a colleague needs you to visit a website to check the content and provide your opinion.
Trust 🤝
Provide sensitive information – a colleague needs you to reveal sensitive information to help them with a task.
Is the email unexpected? Does it convey an undue sense of urgency? Does it ask you to break policy?
- Slow down and think.
- Check the sender details.
- Call the person you think the email is from and ask them. Call them using a known contact number.
✔️ Step 3: Check links or attachments
Links can be displayed in their raw format (www.google.com) or as a hyperlink (this). They can also be disguised or shortened, like this https://bit.ly/3yJanNJ.
To see the true destination of a link, hover your mouse over it.
Or, if on your phone, do what Ian did. Touch & hold the link to reveal its true destination. This is how Ian noticed the link for mail.com, instead of ncsc.gov.uk.
File extensions – the last 3 or 4 letters after the dot [.] at the end of the file – tell you what a file does. So make sure you inspect them before opening attachments.
Does the email include a link or attachment you don’t recognise?
- Hover your mouse over a link to see its true destination.
- Use VirusTotal.com to check whether or not a link to it’s safe to open.
- Check attachments with your IT or Security team before opening.
After Ian Levy coaxed James Linton out of hiding, the pair teamed up. They co-authored a piece about their experience.
Their aim was to help people spot future fake emails.
Our goal is the same, by telling James’ story like never before.
And what does James Linton have to say about this? See for yourself.
You can get access to all of CybSafe’s story-style training for free. Check out how they could supercharge your security awareness activities here!