Rewind
All the content from last year’s PeepSec, Impact and flagship industry events
Oh, Behave! The annual cybersecurity attitudes and behaviors report
Cracking the human cyber risk codeCybSafe and the National Cybersecurity Alliance join forces to decode how behavior and attitude shape security outcomes.Ever wondered how much people fret about online security and if it shapes their online behavior? Curious about...
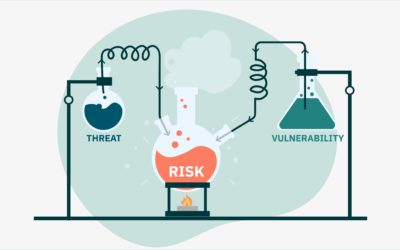
The difference between ‘risks’, ‘threats’ and ‘vulnerabilities’
A cheat guide for security awareness professionals If you’re a security awareness professional, or in the business of managing human risk, it’s important to understand the difference between risks, threats and vulnerabilities. It’s also important to understand the...
On demand webinar: Oh behave! the findings
ON DEMAND WEBINAROh, Behave! The findings The experts unpack the 'Oh, Behave! Cyber Behaviors and Attitudes Report 2023’ What do people really think about cybersecurity? How does this impact their actions? And how does all of this impact your organization's security...
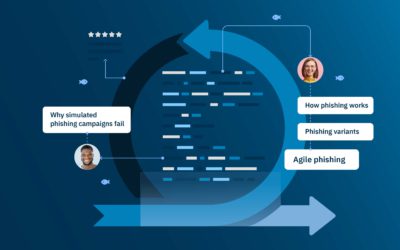
The ultimate people-centric guide to simulated phishing
The ultimate people-centric guide to simulated phishingRun simulated phishing campaigns that reveal what click rates and report rates can’t - what’s driving user riskExecutive summaryGone phishingHow phishing worksPhishing variantsPrevalence & trendsWhy simulated...
On demand webinar: Business email compromise: evolved
ON DEMAND WEBINARBusiness email compromise: evolved“Hey ChatGPT, I’m a CEO and I need my finance director to make a payment urgently. Write me an email!”A new generation of business email compromise (BEC) beckons. BEC is spreading across instant messaging services,...
The game-changing impact of data-driven human risk management
Human risk management: The definitive guideMeet the trail-blazers redefining the security awareness & training space…for good!It's all talkUnderstanding human riskWhat this means for youPart 1: It’s all talk Talking about risk in the security awareness or human...
UK workers spill more secrets to AI than they would to friends in the pub
The London Economic
How much do you really know about cybercrime? (UK edition)
Raise the bar: 50 creative Cybersecurity Awareness Month ideas
Inspiration unlocked: 50 Cybersecurity Awareness Month ideas for CAM 2024“Securing our World”Planning for value, impact, and proofFree resourcesTips, tricks, & things to avoidEvery year, a dizzying high number of people face the consequences of cyberattacks. These...
Artificial intelligence and cybersecurity: Opportunities and challenges
Safeguarding the future: AI’s the top priority this Cybersecurity Awareness Month 2023 Recently we held an outrageous event for our SebDB community. As per usual, it was lively and thought-provoking. (N.B.: You can join the fun here.)We asked the community what was on...
CybSafe 2023 autumn release
Introducing: Human risk management metrics and 25+ new features [lazy-video video_id="_Z2TeajYP6A" background_image="https://www.cybsafe.com/wp-content/uploads/2023/09/CYBSAFE-HRM-imagery-video-thumbnail-230904MS-68-1.webp"...
Workers are spilling more secrets to AI than to their friends
TechRadar
Business Exposed: Employees Spill More Secrets to AI Than They Would to Friends in the Bar
Surge in cybersecurity threats as employees: Struggle to identify Generative AI content, with only 21% believing they can discern an AI generated piece of text from human written text. Admit to sharing sensitive information with AI tools that they wouldn't divulge in...
On demand webinar: 30 proven ways to increase security awareness engagement
ON DEMAND WEBINARSupercharge security awareness engagement30+ proven ways to increase security awareness engagementHuman-related security breaches continue to haunt organizations of all sizes. Why? Largely it’s because most security awareness initiatives are...
The surprising damage cyberbullying does to organizations
Bully for you: How cyberbullying impacts your organization's security, and how you can hit back Steve works in HR. He’s the go-to person for many people when they have problems and need support. But Steve has a problem of his own: he’s been dealing with cyberbullying...
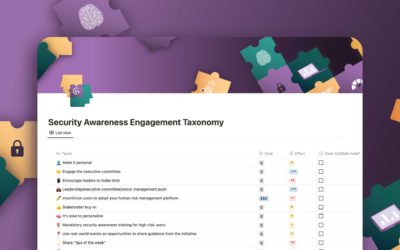
Security Awareness Engagement Taxonomy
Security Awareness Engagement Taxonomy Human-related security breaches continue to haunt organizations of all sizes. Why? Largely it’s because most security awareness initiatives are mind-numbingly dull, failing to captivate the savvy minds of the modern age. Ask...
Employment identity theft: When a personal data heist becomes a professional-level problem
Identity crisis: Identity theft hurts organizations too Picture this: It's 2019, and a woman is charged by the U.S. Department of Justice for using stolen identities to snag employment and healthcare services. But this isn't your typical identity theft case. This...
The thing letting your security awareness training down
What you keep getting wrong about security awareness training Consistency trumps intensity. But when it comes to security awareness training, old-school approaches focus on intensity. Or to put it another way, if there’s a regulatory or compliance deadline on the...
From home sweet home to home safe home: How to maintain security when employees work remotely
“Invite to pay raise briefing? Yes! Finally!” Sarah (a remote worker) leapt up from her dining room table and danced around the room with her dog. Since 2020, Sarah’s been working remotely. At first it was surreal. Then it just slowly became the new normal. ...
The official guide to CybSafe products and pricing
The definitive guide to CybSafe products and pricing In case you haven’t heard, we’re CybSafe, the human risk management platform with lofty ambitions . . . like revolutionizing cybersecurity. But more about that later. We’ve never shied away from a challenge. So,...
The ripple effect: How one phishing attack can cause disaster across your organization
How phishing has catastrophic effects on organizations Phishing attacks are a certified menace. And it doesn’t matter what size or shape your organization is. Or where it is. Or whether you have dress-down Fridays. What’s more, phishing attacks are on the rise. Safe...