The ultimate people-centric guide to simulated phishing
Run simulated phishing campaigns that reveal what click rates and report rates can’t – what’s driving user risk
PART 1
Executive summary
PART 2
Gone phishing
PART 3
How phishing works
PART 4
Phishing variants
PART 5
Prevalence & trends
Part 1: Executive summary
PART 1
Executive summary
In this report, we’ll look at what phishing is, how to guard against it, what companies get wrong about their prevention efforts, and how to right those wrongs.
When we talk about phishing, it’s important to know it works not just because of the believability of the bait, but the various social engineering that goes into enticing a human to take it. Cybercriminals are nothing if not experts in persuasion, and phishing tactics are constantly evolving to make people’s minds up for them. Human cognition and behavior ultimately are what make phishing effective.
…Phishing tactics are constantly evolving to make people’s minds up for them
Technology-based methods of defending against phishing often fail due to limitations and because the human element can’t always be trusted to adequately support them. User-behavior-based protection and prevention methods often fail because training isn’t done adequately or often enough, doesn’t measure what needs to be measured, and often places users in no-win situations.
By being transparent in training, measuring better metrics (beyond click rates and report rates), and running agile simulated phishing campaigns, organizations can be more successful in securing their people and their data against attacks. Here, we’ll go over the elements of a vastly improved methodology for improving security by utilizing your organization’s greatest asset: people. This is how you don’t get caught, and how your organization can squish the phish. See what we did there.
Sorry.
Part 2: Gone phishing
PART 2
Gone phishing
What is phishing? Much to the chagrin of spell checkers everywhere, it’s an intentional play on the word “fishing”, because this hacking method refers to the attackers’ use of certain lures to “fish” for information.
The term phishing dates back to at least 1995. It was first properly coined by prominent spammer Khan C. Smith in the cracking toolkit AOHell. The toolkit “allowed hackers to impersonate AOL staff and send instant messages to victims asking them to reveal their passwords”. Devious.

Image: The splash screen of AOHell.
Broadly speaking, phishing is based on social engineering principles weaponized to deceive people into either revealing sensitive information, or installing malware. At their core: phishing attacks consist of mimicry–either of a person, institution, email address, URL, website, or situation.
As the practice grew in popularity, attacks became more coordinated. In the early 21st Century, criminals targeted internet payment systems and retail banks. By 2005, phishing attacks targeted over a million computer users, totaling nearly $1B in reported losses. Both these totals tripled within three years. Making matters worse, early technical solutions to combat phishing were, in fact, phishing campaigns themselves. #Facepalm.
Phishers have targeted security tokens, social networking sites, law firms, government officials, military installations, insurance organizations, political activists, cryptocurrency holders, financial institutions, retailers, hospitals, oil pipelines, and internet record keepers. They’ve even posed as the IRS to steal social security numbers and other sensitive information from US taxpayers. Phishers have taken over the Twitter accounts of Apple Inc., Elon Musk, and the sitting President of the United States.
All it takes is the right email, sent at the right time, under the right conditions
It is consistently the most commonly reported cybercrime in the world. Its prevalence is in its adaptability. Cybercriminals know exactly what emails to send, when, to whom, and how to trigger victims into engaging in the attackers’ desired behaviors. All it takes is the right email, sent at the right time, under the right conditions. Most phishing attacks are helped along by the very people who have been targeted.
While anyone is susceptible, not everyone will always be susceptible, nor will they be susceptible all the time. That said, too many security awareness initiatives fall woefully short. In this report, we’ll discuss what they are and how to effectively change them.
Part 3: How phishing works
PART 3
How phishing works
Why phishing?
Because it’s easy.
Cybercriminals know human behavior. 82% of all phishing attacks involve the human element. People are often victims themselves, willingly (or are coerced into) offering up credentials, clicking on an enticing link, misusing tools, or misinterpreting commands.
Classic phishing involves sending the victim a link. The link may appear legitimate at first glance, yet they often consist of subtly misspelled URLs or subdomains.
Once the victim arrives on the site, they’re prompted to enter personal information. And of course the criminal can then do whatever they want with it.
Those are the basics of how it works. But the more important question is why does it work?
To answer that, here are three ways hackers get inside your head…and inside your organization.
PART 3
How phishing works
No.1: Nature of the attack
No matter the nuts and bolts of a phishing attack, phishing is social engineering. We define social engineering as the use of deception to manipulate individuals into doing things they wouldn’t usually do, like divulging confidential or personal information. Attackers will often mimic a trusted entity or news source and create a sense of urgency, like threatening to close or seize a victim’s records or bank accounts.
Email remains the most common phishing communication method. Every year, hundreds of millions of phishing emails arrive in inboxes everywhere. Insidious. Cunning. Desperate for attention. What’s so special about the email that people notice and react to? These six categories of emails are highly effective at prompting victims to fall prey to phishing:
-
- Financial/Contractual/Legal
- Social
- Retail/Shopping
- HR/Office communications
- IT communications
- Other or experimental
The allure of clicking on a work email with a subject line like “Q1 Contract Reviews” is just too great to ignore. Especially when criminals can convincingly spoof the CFO’s, CIO’s, or HR Director’s name in the ‘From’ field. There’s an implicit authority in using C-suite names. And it makes it very likely that someone would send sensitive information in response.
And that leads us nicely to our next point.
PART 3
How phishing works
No.2: Influence techniques
As outlined above, authority is a powerful manipulation tactic. But it’s just one of six types of influence techniques employed by phishing attacks. Here’s the full set:
-
- Cooperation
- Scarcity
- Authority
- Consistency
- Liking
- Social proof
These are the most effective methods for getting people to take action, as described by Dr. Robert Cialdini in his seminal 1984 book Influence: The Psychology of Persuasion. These influence techniques drive emotions, which is a catalyst for risk-taking action, and the third reason phishing works.
PART 3
How phishing works
No.3: Emotional drivers
Carrying through that same example, let’s propose your new HR intern gets an email from this authority figure. They say they need help to review the team’s performance, and thus requests the intern send a copy of the customer records by EOD. That urgency drives fear and confusion, which are two core emotions that boost the odds of a successful phishing campaign. Nearly all successful phishing emails prey upon six core human emotions:
-
- Annoyance or anger
- Interest or anticipation
- Joy or excitement
- Surprise or distraction
- Fear or apprehension
- Desire or selfishness

Emotions make us do things. In many cases, they trigger innate human desires–such as to help people or avoid pain. This trigger jumps the final hurdle for us and causes us to act. By injecting urgency into the proceedings, the attacker has further amped up the likelihood their target will comply with their commands.
Part 4: Phishing variants
PART 4
Variants
Social engineering works. Even with just a 3% open rate on phishing emails, that’s more than enough ROI for attackers to keep deploying the tactic. Here, we’ve collected a variety of popular phishing campaign types with which to familiarize you and your teams.
PART 4
Variants
Calendar phishing
Ever seen an unusual calendar event suddenly appear in your calendar app? Someone may have been trying to calendar phish you. These fake events might look like normal, but they can contain malicious links.
PART 4
Variants
Email phishing
Email remains a common and effective phishing channel. Attackers send emails to trick individuals into giving away sensitive information, security permissions, or login credentials. Common targets include financial institutions, email and cloud productivity providers, and streaming services. Attackers use this ill-gotten information to steal money, install malware, or spear phish others within the target organization.
PART 4
Variants
Page hijacking
This is where attackers compromise legitimate web pages. Page hijackers often use cross-site scripting to achieve this. They may insert exploit kits (e.g. MPack) or malicious inline frames which allow exploit kits to load.
PART 4
Variants
Whaling
Like spear phishing, whaling uses customized communications featuring personalized information. These attacks are highly specific, targeting senior executives, high-profile celebrities, or public servants. Attacks commonly include fake subpoenas and customer complaints.
PART 4
Variants
Spear Phishing
This form of attack uses highly targeted emails containing personal details about victims to trick an individual or organization. Spear phishing often targets executives or finance departments. Their access to valuable data, such as information contained in accounting or audit firms, is valuable to criminals.
PART 4
Variants
Voice Phishing
This is where attackers use robocallers to make automated calls to large numbers of people. They often use text-to-speech synthesizers. The calls claim fraudulent activity on a target’s accounts and often use spoof phone numbers to impersonate a reputable institution. Voice phishing attacks prompt targets to enter sensitive information or connect to a live caller who engages in social engineering to steal sensitive data.
PART 4
Variants
SMS phishing + pretexting
Having gained popularity in the early 2020s, SMS phishing uses text messages to deliver the bait. The victim is usually asked to click a link, call a phone number, or send an email to give up sensitive information or make a purchase. SMS phishing takes advantage of limitations in mobile browsers, as well as the relative intimacy of a text message vs an email. Pretexting, meanwhile, is a phishing-adjacent SMS scam. It involves a seemingly innocuous line of dialogue between either a live or AI texter and the attacker’s target. The conversation builds trust.
Part 5: Prevalence & trends
PART 5
Prevalence & trends
Phishing is consistently the most common cybercrime according to the FBI’s Internet Crime Complaint Center. Additionally, phishing continues to increase in prevalence and maliciousness. Verizon estimates 1.2 billion phishing breaches, and approximately 33 million accounts successfully phished in 2022. Approximately one in three phishing attacks now also include a malware installation of some kind.
Initially phishing targeted individuals, but now organizations are firmly in attackers’ sights, too. Businesses reporting phishing attacks rose from 72% to 86% from 2017 to 2020.
As a percentage of overall data breaches, phishing has become one of the most common methods of entry. Here’s a handful of sobering statistics:
-
- Nearly 90 percent of all phishing breaches are financially motivated, the other attacks are related to espionage
- Two in three phishing breaches compromise credentials
- A majority of all social engineering breaches are phishing attacks
The major uptick in phishing includes a burgeoning SMS- and phone-phishing front. Pretexting is now the method du jour of cyber-attackers. If you’ve received an overly friendly text from an unsaved number, it’s likely you’ve experienced it yourself. On the voice front, 5% of us get at least one phishing call per day, according to a recent Verizon report.
Favorite industry targets of phishing attacks include oil and gas, education, finance, healthcare, manufacturing, and retail. Certain regions are particularly susceptible too. In 2022, 99 percent of social engineering-type breaches in the APAC (Asia-Pacific) region were phishing attacks.
It’s not just professional settings facing these dangers though. Phishing is common on social networking apps and sites. The user-inputted personal details are easy to use for identity theft or effective targeting.
Part 6: Why simulated phishing campaigns fail
PART 6
Why simulated phishing campaigns fail
Technical solutions have struggled to address phishing in any meaningful sense. Why else would phishing be such a large, long-lived (and increasing!) threat? As Forbes reported in 2019, phishing problems persist in the face of anti-phishing technologies because they are “a technological medium to exploit human weaknesses”. Technology cannot fully compensate for human risk factors.
82% of all breaches involve human error. Phishing is a human-centric challenge, and it needs a human-centric solution. Simulated phishing campaigns remain the most common way for organizations to test their people’s ability. But this approach woefully underperforms. Despite the billions spent every year, phishing email open rates haven’t measurably decreased over time. More on that later.
PART 6
Why simulated phishing campaigns fail
1) Many organizations rely only on click rates and report rates as success benchmarks
Click rates haven’t budged in years, and they’re not the most accurate gauge of someone’s susceptibility. While higher report rates are often used to determine a program’s effectiveness, it’s far from a gold-standard benchmark. It’s helpful to run a phishing campaign to get a baseline, provide training, and run another phishing campaign to gauge improvement. But if you’re only measuring click rates and report rates, you’re missing a lot. These metrics don’t tell you why people click, or why they report.
PART 6
Why simulated phishing campaigns fail
2) Simulated phishing campaigns are often run in secret
No academic research has proven secrecy advantageous over running simulated phishing campaigns out in the open. We believe this is because a secret phishing simulation doesn’t help people make sense of the information at the point of attack. (And, of course, who wants to be under secret surveillance for two months just to “see how things are going”? How dystopian.) Secretive simulations also fail to instill a mindset of phishing being a constant possibility. With 1.2 billion reported phishing breaches every year–tens of millions every day–people really are always being phished. That’s the important takeaway and the most real reflection of risk. Finally, these secret campaigns create mistrust. They make people hesitant to report concerns or ask for help. So, secrecy leaves your organization even more vulnerable.
PART 6
Why simulated phishing campaigns fail
3) Simulated phishing campaigns are also problematic because they’re too realistic
By enticing people to click on what seems like regular emails, you’re not training your team on how to spot danger. Instead you’re essentially running an email marketing campaign. For example, if someone’s expecting an Amazon delivery (and we know most of you probably are right now), and you send them a phishing email from “Amazon”, they’ll click on it. All you’ve discovered here is you’re good at designing phishing emails.
PART 6
Why simulated phishing campaigns fail
4) Additionally, most simulated phishing campaigns are too short in duration
If a simulated campaign’s too short or doesn’t reach everyone in the organization, you’ll never collect enough meaningful data. If you don’t run campaigns frequently enough, you won’t be able to adapt to shifting criminal tactics. In this respect, one-and-done campaigns can often “fail”. The planning and preparation time outweighs the overall usefulness. Instead, it helps to continuously phish your people … because that’s what criminals are doing.
PART 6
Why simulated phishing campaigns fail
5) Finally, assigning dull, old-school training as a response to someone “failing” a phishing test feels like punishment
If you want people to take something away from training, it should spark excitement and curiosity as people learn new information and skills. Assigning security awareness training immediately after someone clicks on a simulated phishing email may feel logical, but it leaves a bitter taste. No matter your intentions, the sensation of punishment harms people’s ability and desire to recognize and report future attacks.
Part 7: The right approach: Agile phishing
PART 7
The right approach: Agile phishing
When you put your people first, your organization can only stand to benefit. But what does “putting people first” mean in the context of phishing simulations? It means designing them with your people in mind. Focusing on what simulated phishing campaigns can do for your people, rather than your organization, allows you to better demonstrate an increase in their ability to spot and report attacks. This, in turn, allows you to prove a reduction in your phishing-related human risk. So: think phishing? Think people.
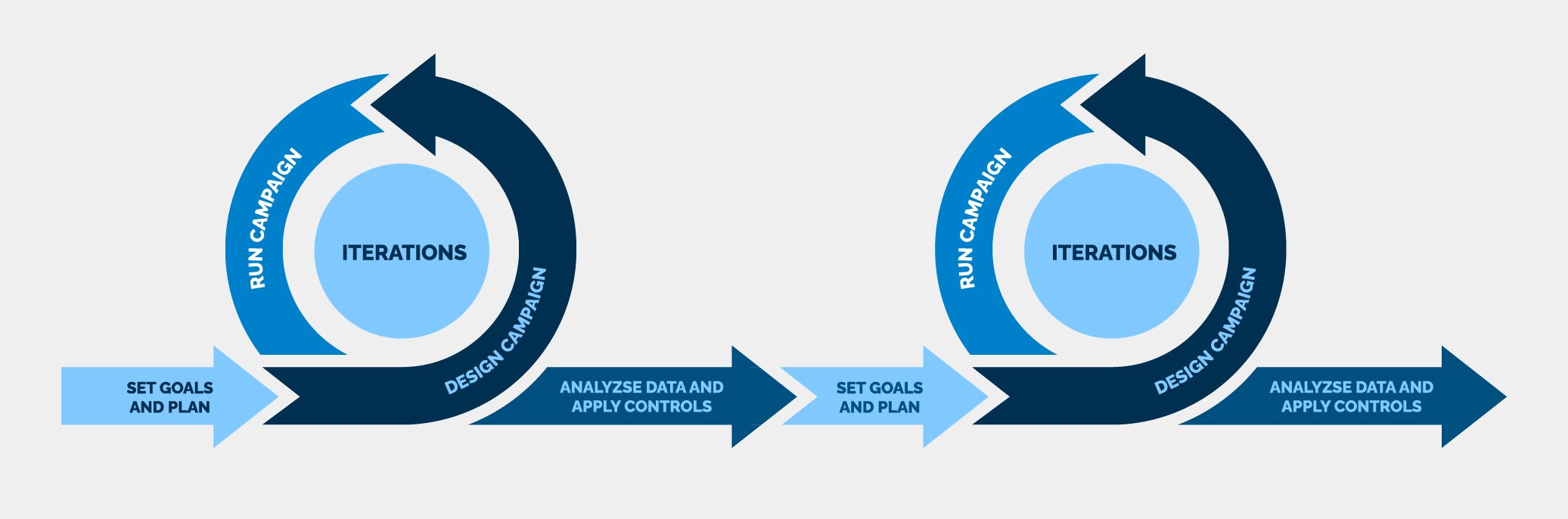
To truly center your people, adopt an agile methodology for your phishing simulations and training. Embracing agile principles fosters active engagement and continuous improvement. Here’s a framework we recommend to get the most out of your simulated phishing campaigns.
PART 7
The right approach: Agile phishing
Step 1: Goal Setting and Planning
Goal setting and planning. Not planning and goal setting.
Before you plan your simulated phishing campaign, you first need to know what you want to achieve. Pick your destination, then map out the route.
Goal setting
Be ambitious and set the bar high. It’s better to do your best and fall a little short than to set the bar low and lull your workforce into a false sense of security:
-
- I want to decrease the number of security incidents linked to phishing
- I want to understand what types of phishing emails my people are most likely to engage with
- I want to increase engagement with cybersecurity across the workforce
- I want to increase my people’s dwell time on phishing emails
- I want to increase my people’s ability to spot and report genuine phishing attacks
Once you’ve set your goals, you need to flesh them out a little. Figure out the questions you need to answer at the end of your phishing campaign. They’ll help you determine whether you’ve met your goals.
-
- I want to decrease the number of security incidents linked to phishing: What are the number of confirmed security incidents linked to phishing?
- I want to understand what types of phishing emails my people are most likely to engage with: Does the category of email make a difference? Are certain influence techniques more successful than others? Does this vary by role, department, seniority or location?
- I want to increase engagement with cybersecurity across the workforce: Are people talking about cybersecurity? Is everybody involved? Are people more comfortable with simulated phishing? How many questions are sent to the security team?
- I want to increase my people’s ability to spot and report genuine phishing attacks: Has the rate and accuracy of reporting increased? Are people clicking on genuine phishing emails less? Are people better able to spot and report more difficult emails?
- I want to increase my people’s dwell time on phishing emails: What are the dwell times between email opening and phishing reporting?
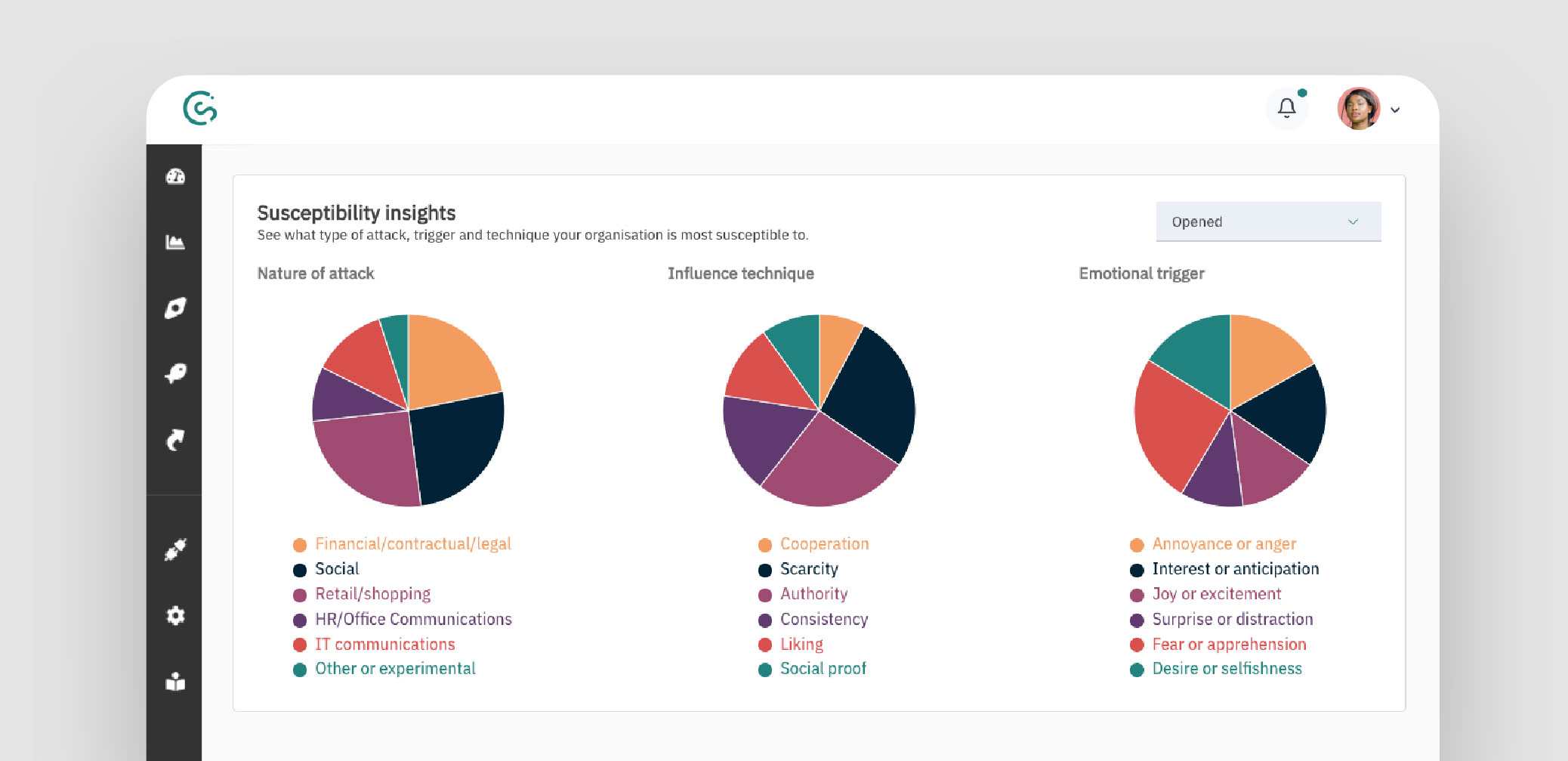
Image: A CybSafe report showing how people engage with simulated phishing emails.
Planning
Next, determine how you’ll measure the campaign’s success. The metrics you measure inform decisions about training and other interventions. Good simulated phishing campaigns shouldn’t just reveal clicks and reports–they should measure why people are clicking, or why they are reporting. Your campaign should gather plenty of data so you can make better decisions about training and other interventions.
-
- Confirmed security incidents linked to phishing
- Time to detect security incidents linked to phishing
- Near misses linked to phishing
- Number of employees asking for help determining the legitimacy of an email
- Policy violations linked to phishing (such as sharing sensitive information via email)
- The total number of repeat clickers
- Employee satisfaction and attitude surveys
- Direct feedback from employees
- Open rates and engagement with phishing-related communications
Managing phishing risk involves changing behavior and changing culture. That’s a tall order, and you’ll need everyone on board. The easiest way to do this is to start from the top and work your way down. To run your campaign organization-wide, you’ll want top-level buy-in. Grab their attention with statistics (as you’ve probably guessed, we recommend the Verizon Data Breach Investigations Report). Make sure management understands the risks and (financial) rewards. What you’re proposing is a strategic initiative that will:
-
- Reduce risk by increasing your people’s ability to spot and report phishing
- Increase cost-effectiveness and return on investment (ROI) by allowing your organization to collect meaningful data so it can make more effective decisions about training,interventions, and behavior change initiatives
- Demonstrate compliance with regulations such as the GDPR, NIS Directive, CCPA, and NYDFS Cybersecurity Regulation, etc.
Calculating your return on security investment
While stats will get you in the room, money talks. So do the math and show them how much money your campaign will save. Here’s how…
1) Single loss expectancy (SLE)
The SLE is the average amount lost per phishing attack.
SLE = Value of assets likely to be impacted by a successful phishing attack × Potential percentage of loss to your assets by a successful phishing attack
E.g.
-
- Asset value likely to be impacted by a successful phishing attack: $1m
- Potential percentage of loss to your assets by a successful phishing attack: 1%

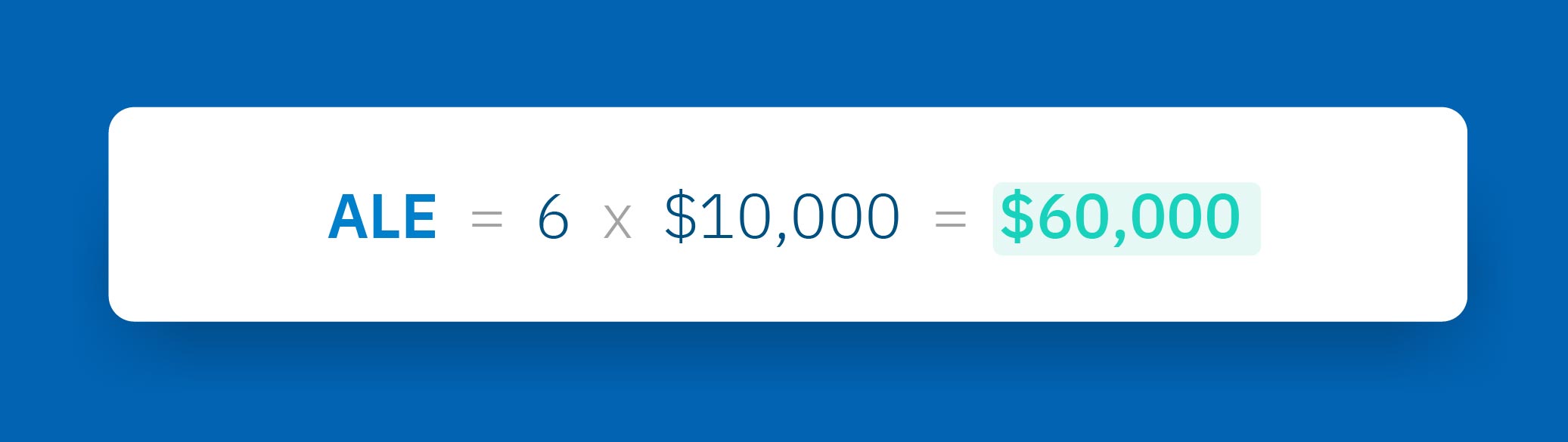
2) Annual loss expectancy (ALE)
The ALE is the loss caused by successful phishing attacks each year.
ALE = Number of successful phishing attacks per year × SLE
E.g.
-
- Number of successful attacks per year: 6
- SLE: $10,000
3) Modified Annual loss expectancy (mALE)
The mALE is the loss caused by successful phishing attacks each year, after you’ve implemented your security programme.
Data from the CybSafe platform shows 90% of users no longer exhibit high-risk phishing behavior after a CybSafe behavior intervention.
Applying this to our example, we can calculate the mALE. This is done by multiplying the ALE by the percentage of unavoidable attacks. In this case, 10%.

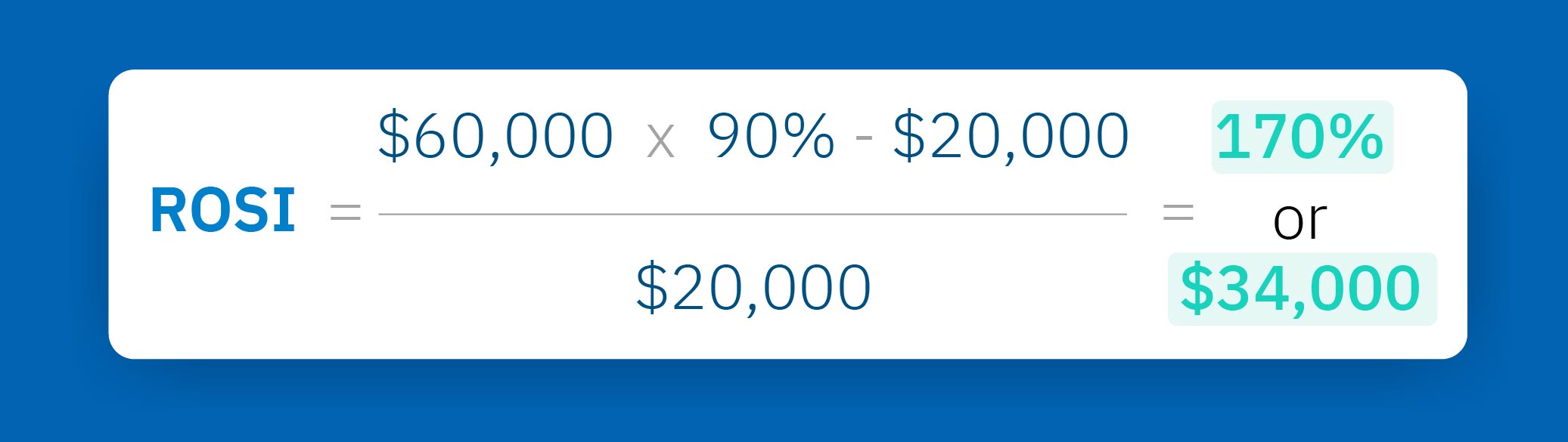
4) Return on security investment (ROSI)
The ROSI is the percentage your security programme is expected to save each year.
This is worked out by taking the ALE ($60,000), multiplying it by the mitigation ratio (90%), subtracting the cost of the security programme ($20,000), and then dividing it by the cost of the security programme ($20,000) to get a final percentage.
In this example a $20,000 investment in a solution such as CybSafe would generate a 170% return. In other words, you would be saving your organization $34,000 per year. Hero.
You may not get the level of support you want immediately, but smaller-scale can still have tons of value. As long as you can start with something you can prove it works and pitch the idea again.
Once you’ve pitched to the top brass, you can spread the word far and wide through the organization. Messaging is the difference between success and failure. You’ll likely need the support of your communications team.
You don’t have to be too prescriptive. Don’t tell them what to say. Simply explain the key messages you want to convey at each stage and the challenges that need addressing. Make use of existing communication lines, newsletters, and intranet services.
HR & other employee representatives
Some additional advice as you prepare your messaging: Phishing is a sensitive subject. This is especially true with HR and other employee representatives, like labor unions. They’re right to be wary. Some organizations punish people who fail simulated phishing campaigns. This can lead to discrimination claims and other tricky legal issues.
Legal
Remember, you’re going to need some personal data for this to work (names, roles, departments, and locations). The data you collect during your campaign will be a form of profiling. It will be low-level, and there is a strong organizational benefit for doing so. But the sensitive personal data generated will be minimal, so it shouldn’t be an issue.
Let your legal, union, and HR teams know ahead of time. Explain how you’ll involve everyone at every stage of the process. Explain how this exercise will increase people’s ability to spot real malicious attacks in both their professional and personal lives. Let them know early so they can get comfortable with the idea.
PART 7
The right approach: Agile phishing
Step 2: Designing the campaign
The most common mistake in security awareness is encouraging people to perform security behaviors before understanding why those behaviors don’t happen already.
If designed right, simulated phishing campaigns reveal why people are clicking and reporting. You can use this information to make informed decisions about training and other controls. We cannot emphasize this enough.
You want people to report phishing emails, and people need to be able to report phishing emails without friction. Adding a “report” button makes it easy (recent research suggests making it red increases use). Beyond that, it’s important to follow up with positive incentives. A “thank you” message after people report will suffice. So too will entering people into prize draws and issuing gifts to top reporters. It’s unsurprising what a show of gratitude can do to boost motivation and reinforce good security behaviors.
The most common mistake in security awareness is encouraging people to perform security behaviors before understanding why those behaviors don’t happen already
Once you’ve got a reporting mechanism, you want a simulated phishing testing tool. You don’t need an expensive solution to do this–a great free option is GoPhish. All the behavioral mapping and data analysis can be done with a spreadsheet.
Remember section 3, “How phishing works”? Remember the nature of attack, influence techniques, and emotional drivers? This is what’s going to set your campaign apart.
You can use the same techniques to figure out why people click/don’t click/report/don’t report. There are easy ways to do this, too:
-
- Templates
- Point-of-click surveys
- Follow-up surveys
A quick note on terminology:
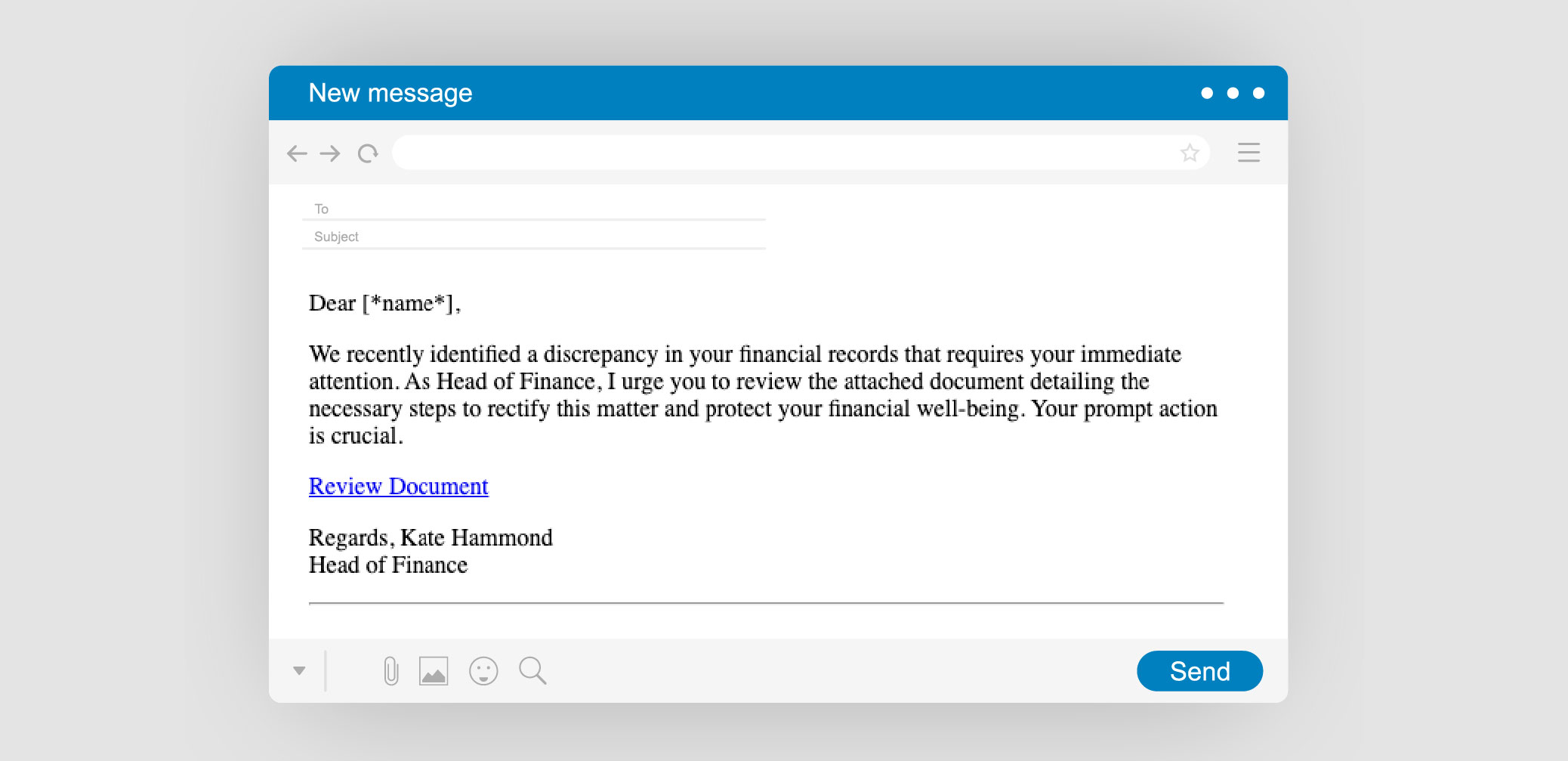
– Templates are your phishing simulation emails, designed to mimic real malicious emails.
– A landing page is where people are taken to after clicking a link in the phishing email. It usually includes a data capture form or a download button.
– A message page is the page people are taken to after a link is clicked, a file is downloaded, or data is entered. This page is used as a “teachable moment”, showing the steps that should have been taken instead of what happened.
Templates
You can use templates to measure emotional drivers by writing influence techniques into them.
Start by deciding on what types of email you want to test. For example, you could test ‘internal communications’ or ‘social invitations’. Then pair these with your chosen influence techniques. How far you take this is up to you.
We’d suggest starting small. Pick a few things to test. And adapt as you learn what people respond to.
Point-of-click surveys
Surveys are another way to measure what people feel when they interact with phishing emails.
Point-of-click surveys seek feedback right after a high risk action is carried out. You can embed them into messaging pages as multiple choice options, or as free-text entries. If you go with free-text, consider how you’re going to analyze the qualitative data generated, and the time you’ll need to do this.
Make sure survey questions are open, not leading, so that responses aren’t biased.
-
- Leading: Did this email make you feel scared?
- Open: How did this email make you feel?
See the difference?
Follow-up surveys
The simplest option. Surveys are sent to clickers along with a copy of the email they clicked on. Above considerations apply.
Remember, you’re running your campaign to understand the reasons behind your people’s security behaviors so you can make better security decisions. That means designing your survey to encourage transparency and engagement.
And how do you do that? By addressing 3 Ps: purpose, punishment and productivity.
-
- Purpose: Make sure everyone understands why they need to complete the survey. Your people are more likely to engage if they appreciate the value their efforts will bring to the organization. In a nutshell, it means being transparent with your people.
- Punishment: We talked about how phishing test results often trigger punishment—or at least something that feels like punishment—and how that can breed resentment and mistrust. So, make your stance on punishment clear to your people. And let them know that their responses won’t be used against them.
- Productivity: We’ve all been there. When there aren’t enough hours in the day. Deadlines are looming. And your manager still needs you to do something. Something that gets in the way of your productivity. Don’t make your survey an obstacle. Keep it short. Keep it simple.
A great tool to use for surveying is Typeform. Typeform allows you to create beautiful looking surveys. Typeform’s conversation-style forms keeps the audience engaged. As a result, you get more thoughtful responses, and higher completion rates.
PART 7
The right approach: Agile phishing
Step 3: Running the campaign
Let people know you’re starting your campaign. Remind them. Then, remind them again. By keeping them in the know, you’re not just increasing awareness about your phishing campaign, you’re increasing awareness about phishing. That’s a good thing.
Do you know what else is a good thing? Not pushing people into the deep end of the swimming pool. Start with easy-to-spot emails. Obvious-to-spot links and “virus.exe” attachments are fine. Remember, this is about helping people spot the signs of a phishing email, so they should be pretty obvious. Here are some other textbook examples:
- “From” details not matching “sender” details
- Requests people normally don’t get
- Unusual links or attachments
- Bad grammar and misspellings
- Unfamiliar greetings
Once people master the basics, you can adjust the difficulty level. Feel free to start small and scale up, embrace radical incrementalism, and make improvements as you go.

Just start!
A hurdle security teams often fail to clear is the belief that things have to be perfect before pressing “go”.
Unless you foresee your campaign doing reputational damage, creating confusion, or increasing security risk, just start! Start small, start scrappy. Don’t hold off on the account that not everything is how you imagined it to be. Embrace radical incrementalism, and make improvements as you go.
Failure to do so means your risk sits unmanaged. That’s a bad thing.
PART 7
The right approach: Agile phishing
Step 4: Analyzing data & applying controls
Refer back to your goals and metrics and get to the analysis. Look for patterns. Some people will be more susceptible to certain categories of emails and influence techniques, so take note of this.
Consider segmenting your data by departments, roles, locations, seniority, and times (of day, week, and year). Of course, it’s going to take a while to gather all the data you need. To form a full picture you need to start early and run your campaign continuously.
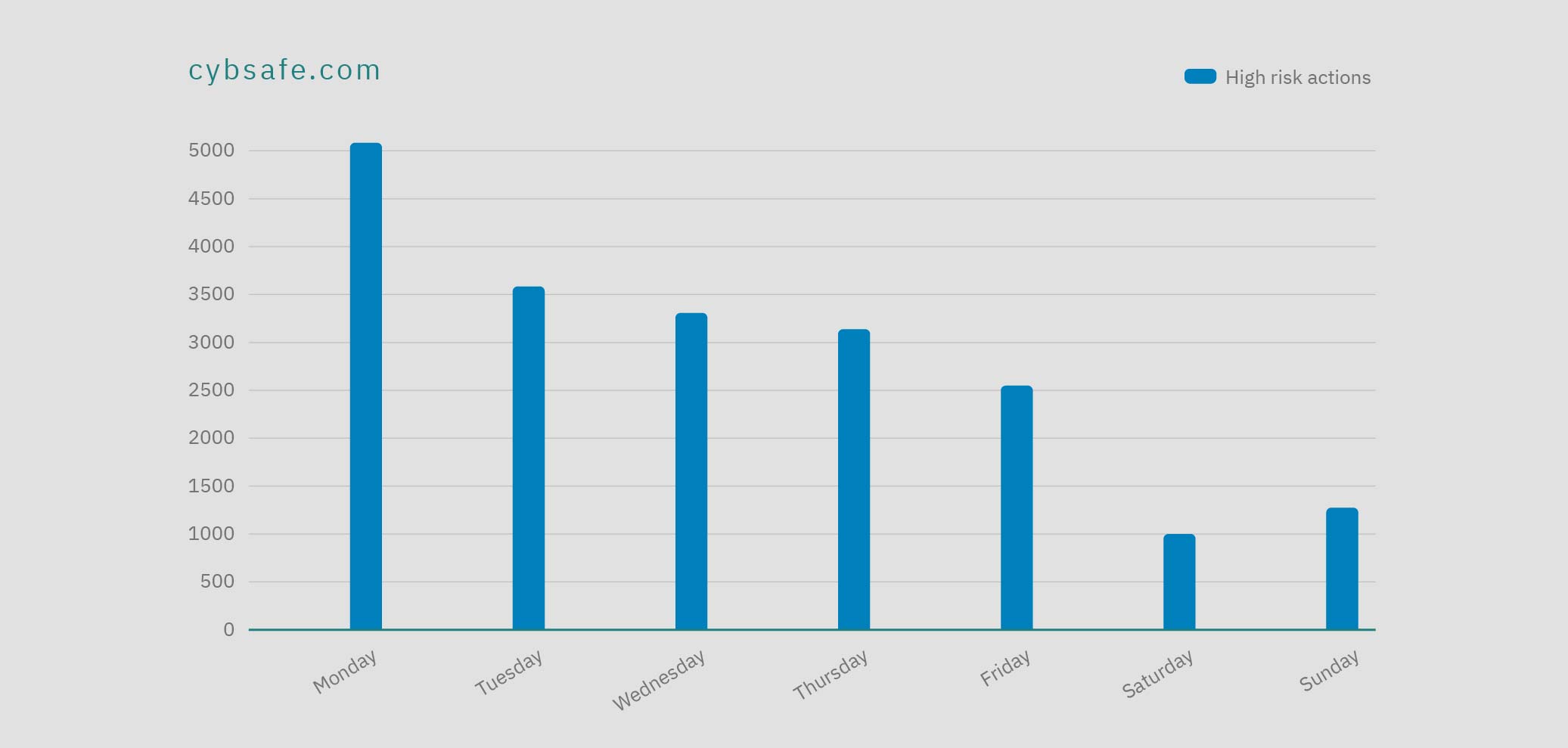
Image: CybSafe data showing high risk actions with simulated phishing emails by day of the week.
Intelligent training
Modify your campaign to include intelligent training, where you can personalize by country, department, level, or skill level. It’ll give you an even greater understanding of where patterns lie and where additional training opportunities are required. Even some personalized training is better than none.
Real-time support
If your people are engaging with simulated phishing emails a little more than you’d hoped, consider offering real-time support. Providing support in the moment of decision-making can help cultivate good habits.
Digging into the data will tell you where and when to provide the most support. For example, what times (of day, week, year) do people click most? Send reminders and nudges at these times. Emails, browser notifications, and SMS messages are all effective.
CybSafe data shows the time people are most likely to click on a phishing email is 0800 on a Monday. Sending a nudge, alert, SMS, or email to remind people at 07:45 would be a great start to your real-time support!
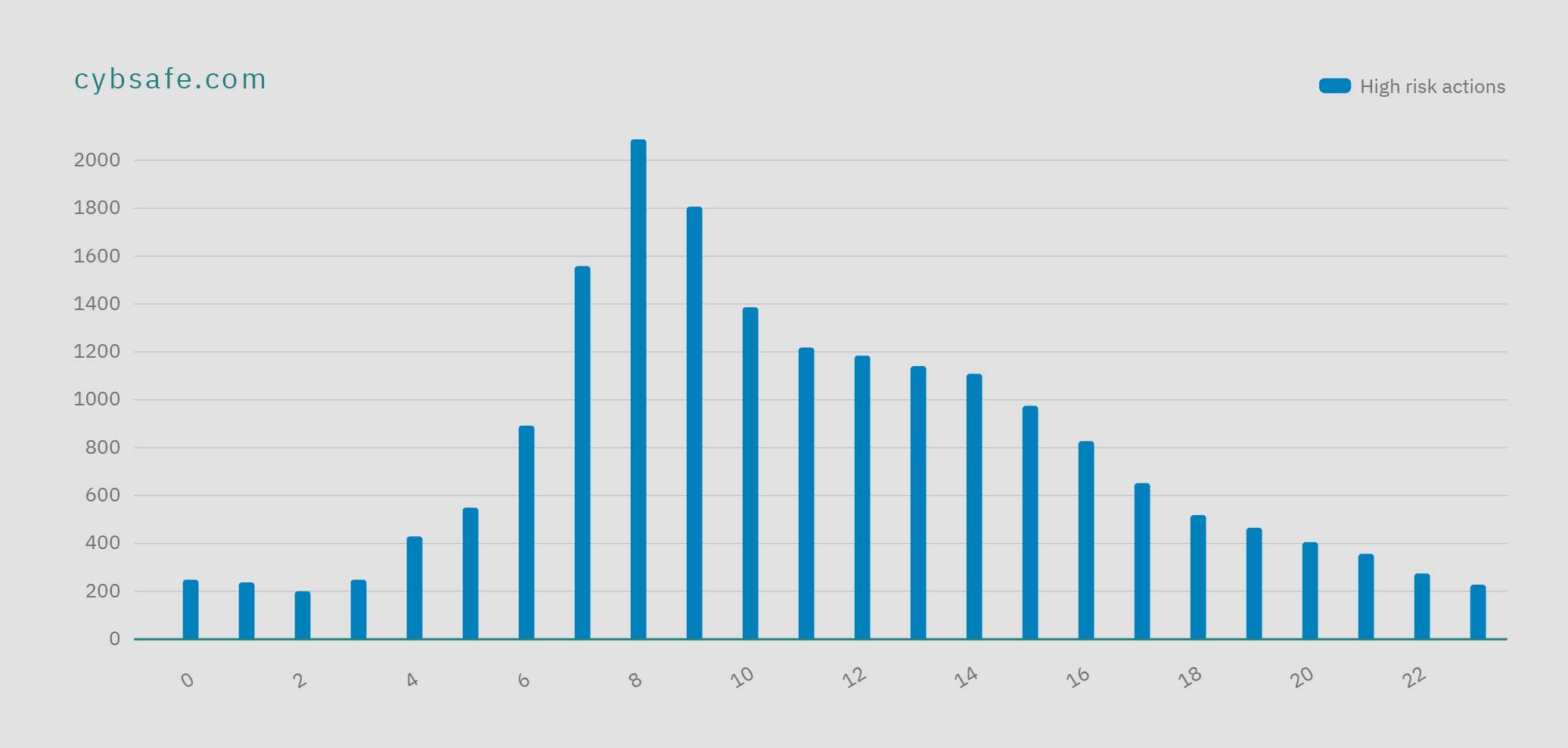
Image: CybSafe data showing high risk actions with simulated phishing emails by time of the day.
“I will never…” lists
“I/We Will Never” lists lay out the things management will never ask people to do. That way, any requests that match the list instantly raise a red flag.
Let’s look at an example:
You’ve picked up that the people in your Finance Department are overly susceptible to phishing emails falling into the legal category. It’s the kind of emails that use authoritative language and evoke panic.
You ask the department heads to list the things they will ask someone in Finance to do, and note how they will make the request. So, a manager will, say, send an expense claim, but only on the first Friday of each month and only to a specific email address.
You also ask the department heads to list the things they will never ask someone in Finance to do. Things like asking someone to disregard protocol, issuing ultimatums or using language that evokes panic. This list can supplement training and be used as a great reference tool.
Here’s the list we use at CybSafe:
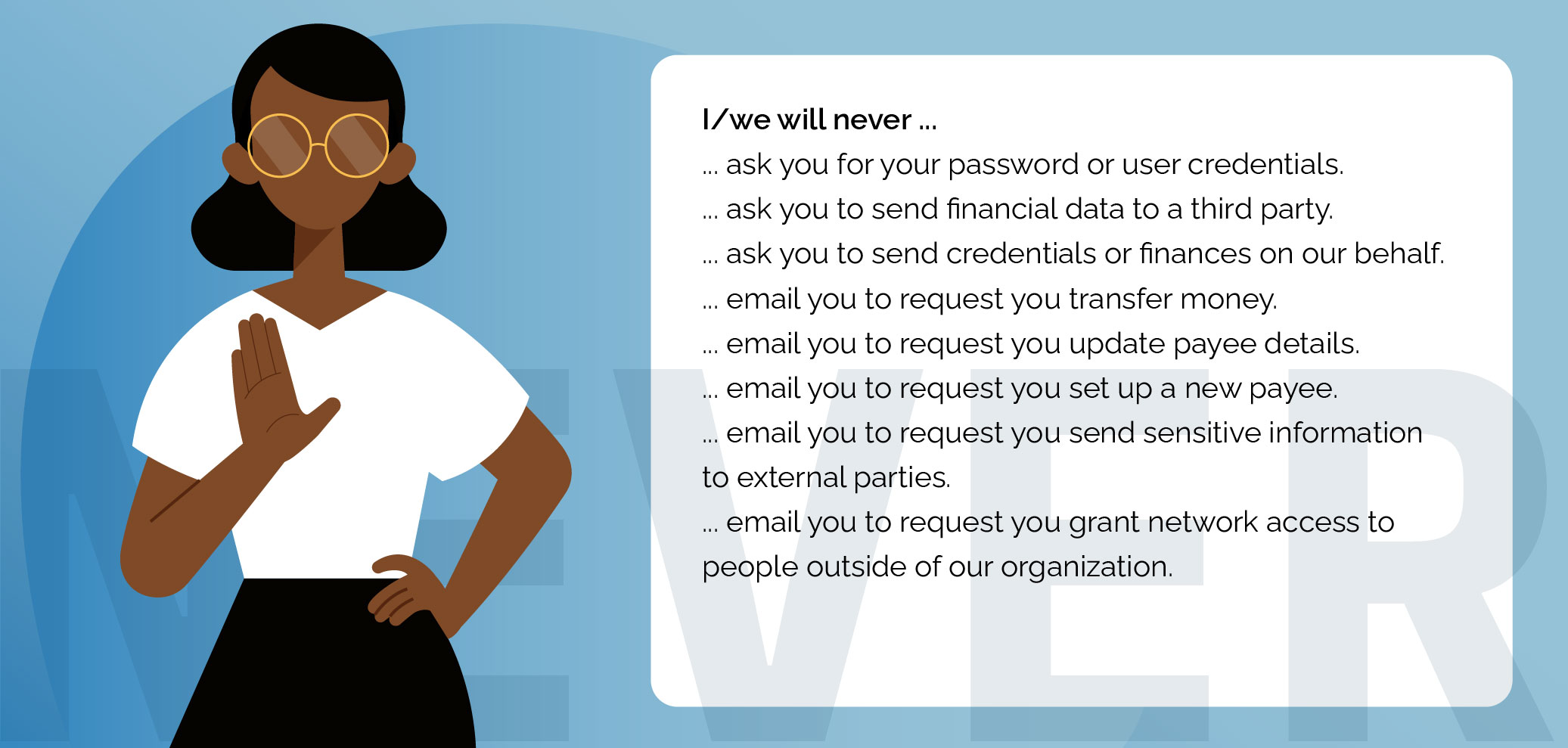
Image: The “CybSafe will never…” list.
PART 7
The right approach: Agile phishing
Step 5: Iterating
Remember early antivirus programs? They were primitive. Each time you wanted to run a scan, you had to press the “scan” button. Nowadays things are different. Modern endpoint protection programs are always on, working away in the background, collecting data, learning, and adapting. Simulated phishing efforts should reflect this constant adaptability—because attackers definitely do!
Also, if you don’t iterate, you’ll quite literally repeat your mistakes over and over again.

So, see what worked, and, if you must, go back to the drawing board. Review your goals and plan, tweak interventions, and realign your campaign to reflect those changes. Ultimately, that’s what the Agile Phishing methodology is all about—getting better, continuously.
Part 8: Final words
PART 8
Final words
Phishing remains popular because it works and because most training to thwart it doesn’t. Essentially, criminals remain better at communicating with your people than you do.
Essentially, criminals remain better at communicating with your people than you do
Phishing might be a cyber-threat, but it doesn’t work without the human element. Thus, technology shouldn’t be your only form of defense. Train your workforce the right way to watch out for phishing, and your diligence will be rewarded in fewer breaches. The right way starts with analyzing the right metrics, so make sure you’re prepared to measure more than click rates and report rates.
Stop running your simulated phishing campaigns in secret and get them out in the open. And start running them more often and for longer, so you encourage constant vigilance. Stop making simulations too realistic, so you can meet people where they’re at on security education journeys. And stop punishing people when they make mistakes. Use positive incentives and reinforcements, and help them understand why mistakes happen and how to better prepare in the future.
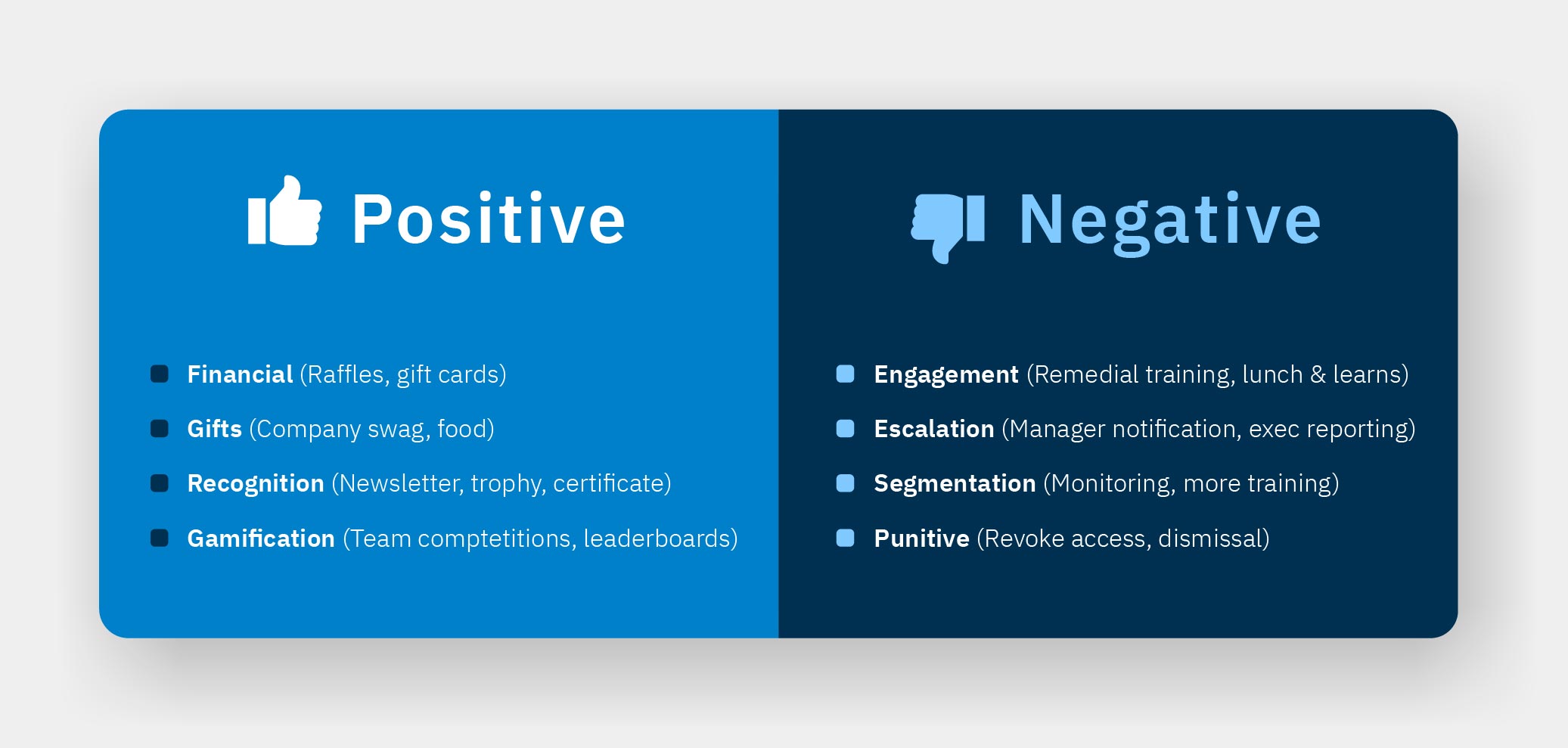
Image: Positive and negative incentives.
Set clear goals, make workable plans, gain organizational buy-in, and iterate on the fly. This approach makes simulated phishing campaigns an integral part of your broader cybersecurity measures. You’ll have no problem easily demonstrating the clear ROI in terms of morale, uptime, and the all-important bottom line.
Phishing is successful because it targets human nature. The best defense is working with people, not against them, and by giving everyone the information they need to collectively succeed. That and allowing them permission to fail, learn, and try again in a positive, safe way.
CybSafe PHISH simulates modern-day threats, and supports people in lowering their phishing and ransomware risk.
To help address risk on all fronts, PHISH combines seamlessly with our other products, giving you a truly holistic approach to phishing and ransomware risk reduction.
